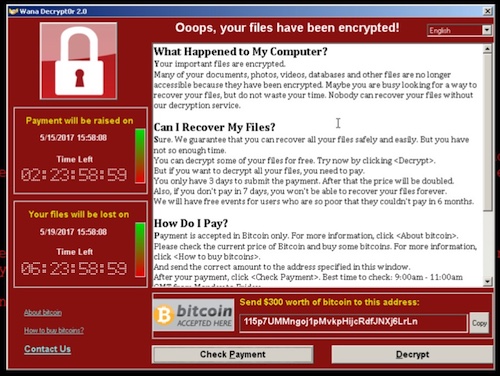
The malicious ?ransomware? attacks that seized computers worldwide Friday and held those systems hostage are likely to worsen this week as millions of people return to work – forcing them to discover the hard way whether they have been affected, security analysts said.
With much of the world still reeling from the digital breach that prevented people from receiving hospital care, a second wave of what European officials have called ?the biggest ransomware attack ever? could be devastating.
?They?re going to turn on their computers in the morning and find out if they were protected or not,? said James Barnett, a security expert at Venable and retired Navy Rear Admiral.
The software, which first affected Britain?s National Health Service before spreading to as many as 150 countries, locked down victims? computers and threatened to delete their files unless they paid $300. It primarily targeted users of Windows XP, an aging operating system for which Microsoft largely ended support in 2014.
Much of the potential damage from Friday?s attack was quickly contained by the efforts of a 22-year-old security researcher, who goes by @MalwareTechBlog on Twitter. The researcher discovered that the unnamed attackers had accidentally included a ?kill switch? in their software that would allow the owner of a particular website to stop the attack. By paying about $10 to acquire the domain name, the researcher was able to thwart the malware.
But that victory could be short-lived, experts said, because the software, known as WannaCry or Wanna Decryptor, is likely to be modified soon and continue its spread in a slightly different form.
For IT workers and security researchers, the episode highlights the challenge of fighting an ever-mutating foe whose motives are rarely clear.
WannaCry is the most high-profile example of a type of attack that analysts have been predicting would surge in 2017 after a substantial uptick in such attacks last year.
?If you looked at what the biggest trends all the security companies were highlighting at the beginning of the year, ransomware was in all of their lists,? said Peter Warren Singer, a technologist and senior fellow at the New America Foundation. He added that interventions by independent researchers such as @MalwareTechBlog highlight the benefits of supporting private hacking.
?If there is a lesson from that,? Singer said, it?s that ?you want to enable security research and information exchange. You want the curiosity of the good guys to be unleashed as much as possible.?
Among those waking up Monday to a nasty surprise could be government officials, some analysts said. Many public computers still have Windows XP installed, and they could be susceptible to the malware if IT administrators have not downloaded the appropriate security patches.
Some federal agencies have moved more quickly than others to stamp out Windows XP, said R. David Edelman, an Obama administration official who advised the White House on technology matters. How adept each agency has been at upgrading its systems has largely to do with available resources.
?There are certainly still systems in the government that are running XP,? Edelman said. ?Some of them are almost certainly Internet-connected; some of them might be further back-end or otherwise not as vulnerable.?
In 2015, the Navy agreed to pay Microsoft $9 million a year for continued Windows XP support. Since then, officials have sought to end the Navy?s reliance on outdated software by developing a ?Microsoft Eradication Team.? Now the Navy is moving rapidly to transition to Windows 10.
By this point, federal officials largely have a handle on XP, Singer said. But, he added, state and local governments that lack expertise or funding may face greater troubles.
By drawing attention to the shortcomings of legacy computer systems, WannaCry could indirectly drive more demand to companies such as Google and Microsoft that have built massive cloud computing businesses, said Stewart Baker, a former general counsel at the National Security Agency.
?This may well force a lot of legacy systems finally into the cloud, is my guess,? Baker said, ?which is probably where they?re going in the long run ? but they?ll get there faster [now] because the idea of continuing to run XP is not credible.?
In a blog post Sunday, Microsoft chief legal officer Brad Smith said the incident highlights the dangers of stockpiling digital weapons, and called for a ?Digital Geneva Conventions? to govern their use.
?The governments of the world should treat this attack as a wake-up call,? Smith wrote. ?They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world.?
Source: washingtonpost.com
