Potter Electric Signal Company announced its new line of D-TECT Intelligent Conventional Sensors and Bases. Built with the same technology as Potter’s recently released D-TECT Intelligent Addressable Sensors and Bases, they were developed to better address nuisance alarms, improve ease of installation, and provide more efficient testing and maintenance. Featuring Dynamic Threat Emergency Communication Technology, D-TECT sensors achieve adaptive response and reduce false alarms, while a patent-pending photo chamber accurately detects fire and rejects nuisance sources like cooking or dust.
Read More ›POTTER Launches New Intelligent Conventional Sensor and Bases
PKOC at CONSULT 2024 Jason Ouellette and Ed Chandler to Speak

The PSIA announced that two of its members actively supporting the PKOC specification will be speaking at the CONSULT 2024 Symposium. Since its inception, eight years ago, CONSULT has emerged as one of the premier and most unique events in the security industry. The symposium fills a largely unmet need in the security industry for manufacturers and consultants to interact with each other, to better understand security technologies, trends, and techniques as they impact security consultants, and to create an environment for the development of valuable relationships.
Read More ›How Physical Security Professionals Can Understand Unauthorized Drone Activity

Physical security is never an easy job. It’s a high-stakes business. Designing an effective access control strategy requires you to think not only as a defender, but rather as an invader. Protecting your customer requires you to anticipate the actions of a determined, resourceful, adversary. And they are resourceful. The rise of affordable, capable drones presents an ongoing challenge to public and private sector organizations, and the security teams tasked with protecting them.
Read More ›Swann Security Unveils World’s First AI Smart Doorbell with Introduction of SwannShield™ Voice Assistant for SwannBuddy4K

Swann announced the general availability of SwannShield™ – the world’s first AI-powered home security voice assistant. Compatible with Swann Security’s industry-leading SwannBuddy4K™ Video Doorbell, SwannShield™ engages with visitors in real-time across different scenarios, from package deliveries and identifying guests to deterring potential criminals. SwannShield™uses the latest adaptive generative AI technology and user instructions to respond to visitors with natural, realistic, human-like interactions when they press the doorbell.
Read More ›Genetec Announces Powerful New Tools to Help Law Enforcement Securely Share Vehicle Data and Accelerate Investigations
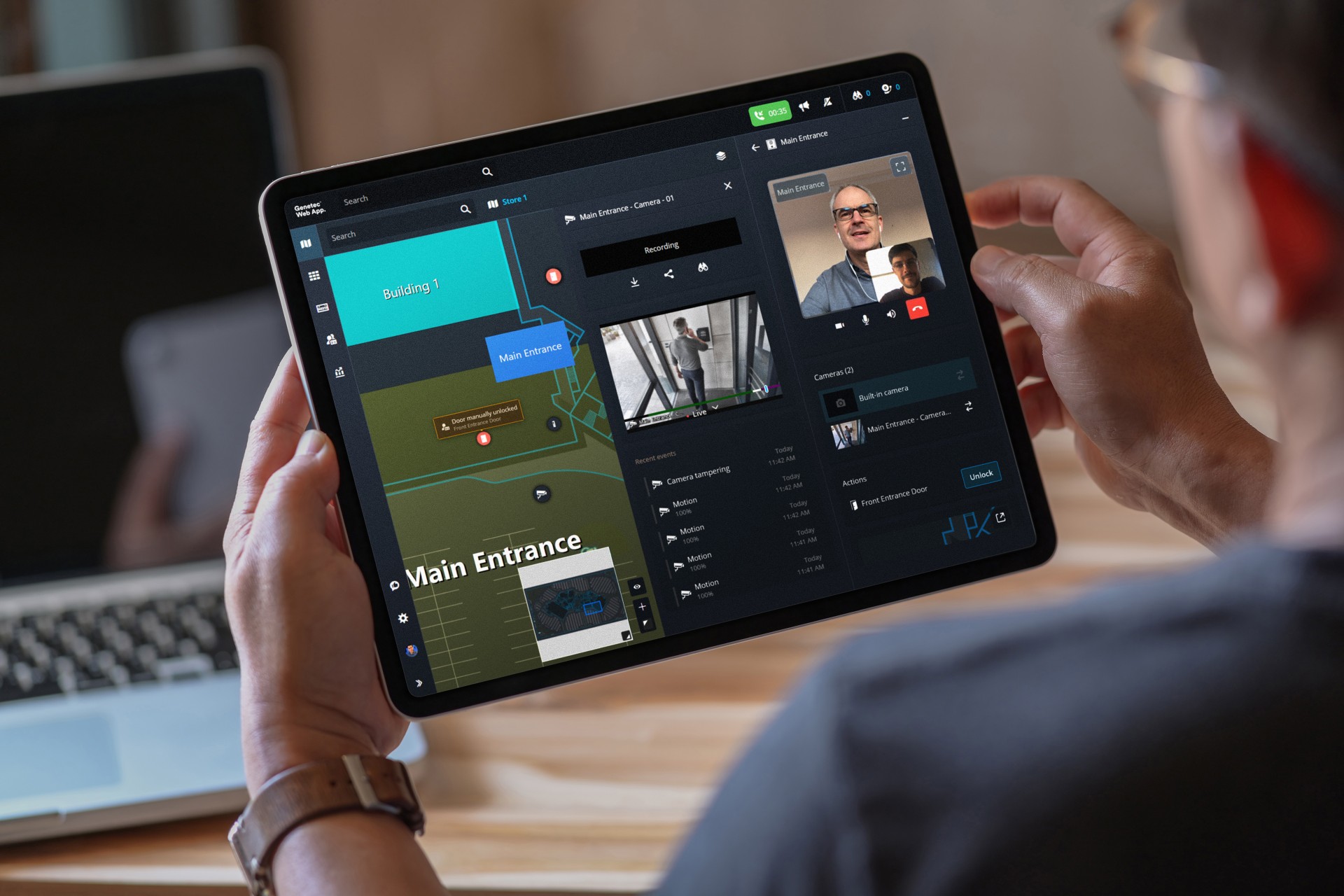
Genetec announced a new feature that enables law enforcement professionals to easily collect, manage, and share vehicle-based evidence captured by AutoVu Cloudrunner™ through the Genetec Clearance™ digital evidence management system (DEMS). Investigators typically rely on various types of data when building a case, such as license plate reads, video footage, and other forensic evidence.
Read More ›Axis Communications Expands Global Presence with First Southern Cone Technology Experience Center in Chile

Axis Communications celebrated the grand opening of its newest Axis Experience Center (AEC) in Santiago, Chile – the first AEC to be constructed within the southernmost part of South America, otherwise known as the Southern Cone.
Read More ›Everon Launches Mavn BI™, Onepoint™, and Sightline™ Brands for Intelligence-Driven, Video Solutions and Account Management Suite

Everon announced today the launch of Mavn BI™ business intelligence, Sightline™ advanced video solutions, and Onepoint™ account management portal as part of a series of differentiating offerings. The launch notably delivers on Everon’s investment made through this year’s acquisition of DIGIOP, a groundbreaking software development company specializing in video and business intelligence solutions, and reaffirms the integrator’s mission to chart a path to growth through technology and innovation.
Read More ›i-PRO Unveils Heavy-duty Aero PTZ Cameras with Edge AI Analytics

i-PRO announced the addition of 19 new models to its Aero PTZ camera line featuring enhanced durability and edge AI processing. Built for extreme weather and environmental conditions, the new, heavy-duty Aero PTZ cameras support up to 4K resolution and feature AI-driven analytics. With a zoom range of up to 40x, the shock-resistant, water-proof Aero PTZ cameras are IK10, MIL-STD-167-1A, and IP66/68 rated for uninterrupted video protection during extreme weather conditions.
Read More ›VIVOTEK Partners with CMS on Cloud Detection Systems to Address Operational Challenges for Antarctic Icebreakers

VIVOTEK successfully partnered with CMS, a leading provider of solar radiation measuring and analysis solutions, to implement an innovative Cloud Detection and All Sky Measurement system. The project aimed at delivering accurate and reliable data for applications such as weather and cloud observations, atmospheric and climate research, solar irradiance monitoring, and irradiance nowcasting for photovoltaic plant.
Read More ›PKOC Bluetooth 3.0 Released Enhanced Cryptography Support

The Physical Security Interoperability Alliance (PSIA) announced its Public Key Open Credential PKOC Bluetooth 3.0 specification at GSX 2024. This is the culmination of a significant amount of work from some of the leading access control companies in order to achieve this milestone. The 3.0 spec features enhanced cryptography, which supports all Bluetooth hardware. In addition, the spec has been optimized to reduce the time it takes to authenticate.
Read More ›i-PRO Awarded Virginia Sheriffs’ Association Procurement Contract to Streamline Access to Mission-Critical Equipment

i-PRO Americas announced that it has been awarded a new procurement contract by the Virginia Sheriffs’ Association (VSA). This contract offers government agencies across Virginia and the United States efficient access to i-PRO’s advanced security products and services through a competitively bid, cooperative purchasing program. The agreement eliminates the need for additional Requests for Proposals (RFPs), allowing public bodies to bypass lengthy procurement processes and acquire essential equipment faster and more cost-effectively.
Read More ›Teledyne FLIR Releases Prism AIMMGen with Synthetic DataGeneration for Automated AI Model Optimization

Teledyne FLIR announced Prism AIMMGen™, its latest addition to the Teledyne FLIR Prism™ software family. Prism AIMMGen is an ITAR-free AI model generation service that enables the automated creation of artificial intelligence (AI) and machine learning (ML) models using synthetically generated data. It offers significant cost and schedule savings for system integrators developing AI/ML products for commercial, first response, and defense applications.
Read More ›AlarMax Celebrates Grand Opening of Albuquerque Branch

AlarMax announces its newest branch location in Albuquerque, New Mexico. This expansion is the latest strategic milestone in AlarMax’s nationwide growth, aimed at bringing high-touch service and cutting-edge technology to more markets across the U.S. A grand opening barbeque will be held on Thursday, October 17, 2024, from 3 p.m. to 7 p.m. at 5901 Pan American Fwy Suite D1, Albuquerque, NM 87109.
Read More ›VIVOTEK’s VORTEX Helps Local Security Leader AVS Reduce 90% of False Alarms and Updates MINI of Portland Operational Efficiency
American Veterans Security (AVS), a local leader providing comprehensive security solutions with over 30 years of experience, serves various clients, including commercial, residential, industrial, construction sites, and automotive sectors. AVS specializes in security monitoring and live interactive video services. AVS’s mission is to offer its clients reliable, scalable, and cost-effective security solutions while maintaining a high standard of service to meet the unique needs of its clients.
Read More ›Genetec Retains World Leader Position in Video Management Software, Analysts Confirm
Genetec announced that it has once again been recognized as the world leader in video management software (VMS) by two leading industry analysts, Omdia and Novaira Insights. According to Omdia’s 2024 Video Surveillance & Analytics Database Report, Genetec has retained its #1 global position in the VMS market while also ranking #1 globally in the combined Video Management Software (VMS) and Video Surveillance as a Service (VSaaS) market.
Read More ›PureTech Systems Inc. Releases New Comprehensive Interface Control Document

PureTech Systems announced the release of its new Interface Control Document (ICD). This essential document provides detailed information on the interfacing requirements necessary for integrating PureTech Systems’ advanced autonomous perimeter detection, tracking, and alerting into third-party C5ISR, VMS, PSIM, and other Command and Control systems. The new ICD is designed to support developers, engineers, and integrators in effectively integrating and deploying PureTech’s autonomous perimeter protection technologies with new and existing security systems.
Read More ›VIVOTEK and ProdataKey Announce Strategic Integration Partnership

VIVOTEK announce its integrated partnership with Draper, Utah-based ProdataKey (PDK). VIVOTEK’s VORTEX cloud surveillance will integrate with PDK access control solution to unlock a comprehensive view of physical security. he PDK.io cloud platform allows for complete system management and control through any web-connected device, anywhere, anytime. With thousands of systems managing tens of thousands of doors for a quickly expanding base of loyal customers throughout North America and beyond,
Read More ›PSIA’s PKOC Demonstrated at GSX 2024

The PSIA had another impressive and compelling demonstration of its PKOC spec at GSX 2024. Some of the leading lock and physical access control (PACS) vendors were able to see PKOC in action, with commercially available readers, cards, and apps all relying on the open specification, showing seamless interoperability. The simplicity of PKOC, ease of integration, and the significant advantage of asymmetric encryption were some of the drivers that were most interesting to the companies and customers who were able to see the demonstration.
Read More ›Quanergy Solutions Introduces Q-Vision F540: A Revolutionary 3D LiDAR Sensor for Industrial Applications

Quanergy announces the launch of the Q-Vision™ F540 3D iToF LiDAR sensor. The Q-Vision solid-state family of sensors extends beyond Quanergy’s acclaimed mechanical M-Series line to optimize automation processes across industries such as logistics and warehouse management, construction, and agriculture with our cutting-edge solid-state technology. The F540 delivers exceptional environmental and vibration performance for both off-road and indoor industrial vehicles, including forklifts, Autonomous Guided Vehicles (AGVs), Autonomous Mobile Robots (AMRs), coupled with its exceptional imaging quality, edge compute intelligence and highly accurate volumetric measurements.
Read More ›Clare Software Update from Snap One Enhances Usability And Security For Integrator Partners and End Users

Snap One, now part of ADI, launched its latest software update for Clare, introducing several new features for integrator partners and end users designed to help increase safety and improve the overall user experience with greater visibility into systems, flexibility, and additional third party integrations. These new updates include FusionPro enhancements, ClareOne Panel and ClareHome App updates, as well as new drivers and integrations.
Read More ›
