Legislative efforts began in eleven cities aimed at requiring police departments to be more transparent about the surveillance technology they use. The bills will also reportedly propose increased community control over the use of surveillance tools. These efforts, spearheaded by the ACLU and other civil liberty organizations, are important at a time when surveillance technology is improving and is sometimes used without the knowledge or approval of local officials or the public.
Many readers will be familiar with CCTV cameras and wiretap technology, which police use to investigate crimes and gather evidence. Yet there is a wide range of surveillance tools that are less well-known and will become more intrusive as technology advances.
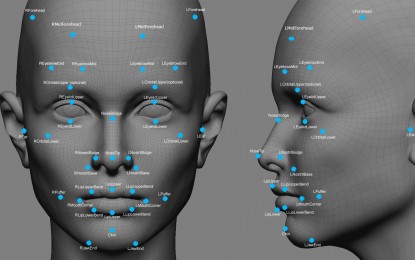
Facial recognition software is already used by some police departments. As this technology improves it will be easier for police to identify citizens, especially if it is used in conjunction with body cameras. But our faces are not our only biometric identifiers. Technology in the near future will make it easier to identify us by analyzing our gait, voice, irises, and ears.
This is concerning given that (thanks to the state of legal doctrine) police are not carrying out a Fourth Amendment search when they analyze your features with biometric tools. As Duke law professor Nita Farahany explained to the Senate Judiciary Subcommittee on Privacy, Technology and the Law in 2012:
If the police use facial recognition technology to scan an individual?s face while in a public place, and that individual is not detained or touched as he is scanned, then no Fourth Amendment search has occurred. Neither his person nor his effects have been disturbed, and he lacks any legal source to support a reasonable expectation that his facial features will be hidden from government observation. He has chosen to present his face to the world, and he must expect that the world, including the police, may be watching.
Even features below your skin may soon be used by police to identify you with ease. British and American Intelligence officials reportedly used vein recognition analysis while seeking to identify ?Jihadi John,? a British terrorist responsible for a string of beheadings in Syria.
Potential terrorism and national security concerns are often cited to justify the secrecy surrounding the ?Stingray.? Stingrays, which work by mimicking cell-towers, collect identifying data from cellphones within range. This data allows investigators to track and identify targets. Although dozens of law enforcement agencies have used Stingrays, their use is shrouded in secrecy thanks in part to FBI non-disclosure agreements. The Federal Communications Commission (which oversees radio-emitting tools) has granted the FBI authority over the regulation of Stingrays. The FBI?s non-disclosure agreements are so secretive that they can require prosecutors to drop charges rather than publicly reveal that a Stingray has been used.
As my colleague Adam Bates has explained, Stingrays are almost certainly overwhelmingly used for routine investigations that have nothing to do with terrorism:
Despite repeated references to ?terrorists? and ?national security? as a means for maintaining secrecy about Stingray use, the data that has been released detailing the purposes of actual Stingray investigations —such as this breakdown from the Tallahassee Police Department that contains not a single terrorism reference— suggests that Stingrays are used virtually entirely for routine law enforcement investigations.
Cell tower simulators can be mounted on airplanes, but advances in drone technology means that flying surveillance tools above cities won?t always require manned aircraft. The prospect of cell tower simulators mounted on huge solar-powered drones capable of staying aloft for months is worrying enough, but as technology improves drones will be getting smaller as well as bigger. Drones the size of small birds have already been developed and used for military operations, and we should expect similar drones to be routinely used by domestic law enforcement in the not-too-distant future.
Source: cato.org
