Advice on how to encourage information sharing while preserving control over access to data is provided in a new special publication from the National Institute of Standards and Technology. NIST Special Publication 800-162 is titled Guide to Attribute-Based Access Control Definition and Consideration.
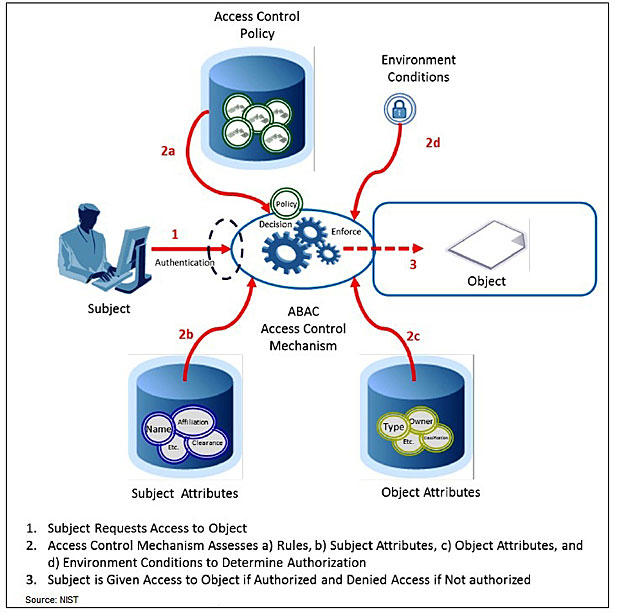
Attribute-based access control, or ABAC, is a logical access control methodology where authorization to perform a set of operations is determined by evaluating attributes associated with the subject, such as a user or employee; an object, such as specific computerized resource; and requested operations.
The flexibility of the ABAC model allows the greatest breadth of subjects to access the greatest breadth of objects without specifying individual relationships between each subject and each object, according to the NIST guidance.
"Access decisions can change between requests by simply changing attribute values, without the need to change the subject/object relationships defining underlying rule sets," says NIST Computer Scientist Vincent Hu, who co-wrote the guidance. "This provides a more dynamic access control management capability and limits long-term maintenance requirements of object protections."
Example on How ABAC Works
Nancy Smith, a nurse practitioner in a hospital’s cardiology department, is the subject, and when hired at the medical center, she is assigned a set of attributes: her name, title and department, for instance. She’s assigned access to an object, in this case, medical records of heart patients.
Resources may receive their attributes either directly from their creator or as a result of automated scanning tools. The object owner creates an access control rule to govern the set of allowable operations; for example, all nurse practitioners in the cardiology department can view the medical records of heart patients. By making the process more flexible, attributes and their values may then be modified throughout the lifecycle of subjects, objects and attributes without modifying every subject-object relationship. NIST says this process provides a more dynamic access control capability because access decisions can change between requests when attribute values change.[…]
Source: databreachtoday.eu
