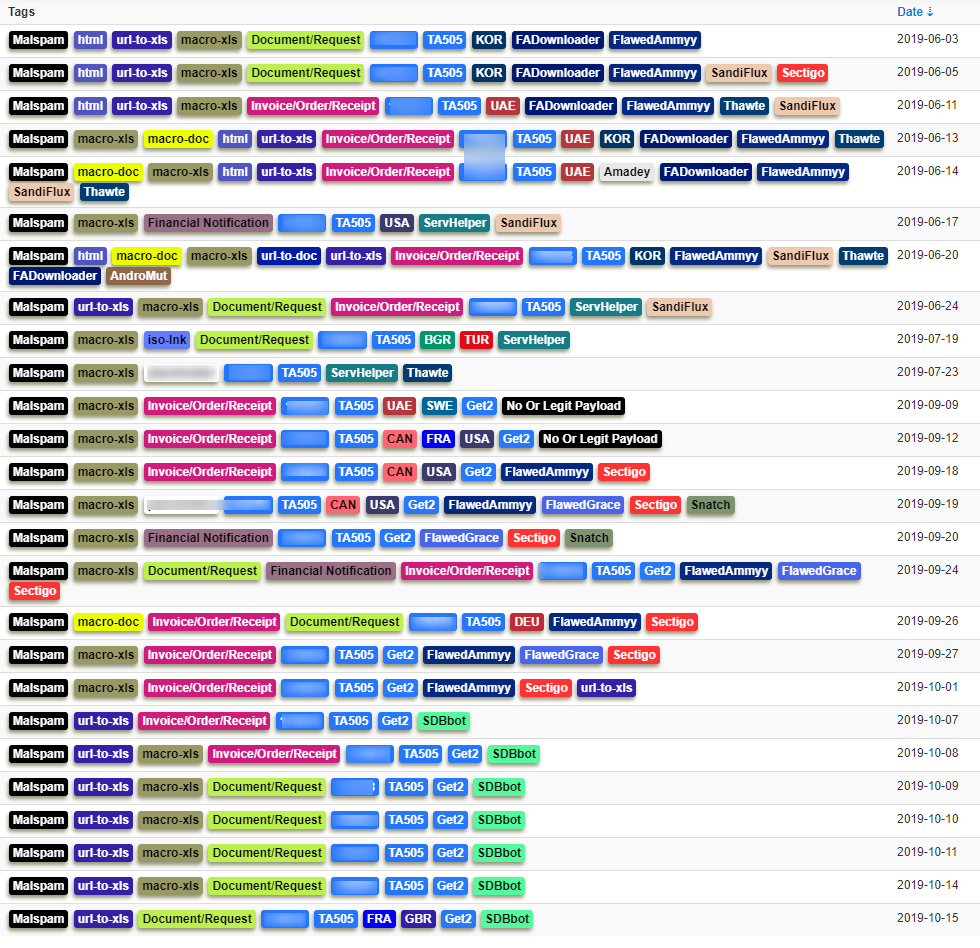
In September 2019, Proofpoint researchers observed a prolific threat actor, TA505, sending email campaigns that attempt to deliver and install Get2, a new downloader. Get2 was in turn observed downloading FlawedGrace, FlawedAmmyy, Snatch, and SDBbot (a new RAT) as secondary payloads.
In this blog post, Proofpoint will detail the tactics, techniques, and procedures (TTPs) associated with these latest campaigns and provide a detailed analysis of Get2 downloader and SDBbot RAT.
These new developments are a continuation of a pattern where, since 2018, Proofpoint researchers observed numerous threat actors increasingly distributing downloaders, backdoors, information stealers, remote access Trojans (RATs), and more as they abandoned ransomware as their primary payloads.
TA505 has been at the forefront of this trend, which began with the distribution of a new backdoor ?ServHelper? in November 2018, and a new downloader malware, AndroMut earlier this year.
Since September 9 2019, Proofpoint researchers started observing TA505 using Get2 as their initial downloader (still at the time of this publication). At first, it downloaded traditional payloads including FlawedAmmyy and FlawedGrace. However on October 7 Proofpoint researchers observed Get2 downloading the new RAT, SDBbot.
In addition to the new malware, these campaigns have continued to innovate in other aspects:
? TA505 remains a serious contender for the top positions in the volumes of emails distributed (most days tens or hundreds of thousands of messages, but sometimes pushing pushing into millions).
? TA505 continues to focus on targeting financial institutions alternating with more widely-targeted campaigns going after other verticals.
? New geographical targeting includes Greece, Germany, and Georgia.
? New Microsoft Office macros are used specifically with the Get2 downloader.
What’s new/cool
? New downloader, Get2, written in C++
? New remote access Trojan, SDBbot, written in C++
? New geographical targeting includes Greece, Germany, and Georgia
? New Microsoft Office macros are used specifically with the Get2 downloader
Implications
? Throughout 2018, Proofpoint researchers observed threat actors increasingly distributing downloaders, backdoors, information stealers, remote access Trojans (RATs), and more as they abandoned ransomware as their primary payload.
? In November 2018, TA505, a prolific actor that has been at the forefront of this trend, began distributing a new backdoor we named ?ServHelper?.
? In June 2019, TA505 followed this with AndroMut, which Proofpoint researchers observed distributing the FlawedAmmy RAT.
? Finally, in September 2019, Proofpoint researchers observed TA505 attempting to deliver email campaigns that install Get2. Get2 is a new downloader distributing, among other payloads, SDBbot (October), a new RAT malware. Get2 and SDBbot are net new discoveries.
? TA505 remains a serious contender for the top positions in the volumes of emails distributed (most days tens or hundreds of thousands of messages, but sometimes pushing into millions).
? TA505 continues to focus on targeting financial institutions alternating with more widely-targeted campaigns going after other verticals.
? TA505 is now targeting Greece, Germany, and Georgia.
Geo targeting
? Greece, Singapore, United Arab Emirates, Georgia, Sweden, Lithuania, US, Canada, Germany, and others
Figure 1: A selected chronology of TA505 malspam campaigns culminating with Get2 and SDBbot in September and October of 2019.
Below are the details of several notable malicious email campaigns.
September 9, 2019
On September 9 Proofpoint researchers observed tens of thousands of emails attempting to deliver Microsoft Excel attachments with English and Greek lures. These emails targeted financial institutions in Greece (a new country target for TA505), Singapore, United Arab Emirates, Georgia, Sweden, Lithuania, and a few other countries. The emails used the following example subjects and attachment names:
- Subject ?HPE INV-02 – Invoice and documents? and attachment ?hpe_s_hp-inv_02.xls?
- Subject ?Need to Apply? and attachment ?dc123456.xls?
- Subject ??